Content by Ali Mirzakhani Nafchi

Virtual Agricultural Economics and Precision Agricultural Advancement Workshop
SDSU Extension will host a virtual workshop covering agricultural economics and precision agricultural advancement on February 26 from 10:00 a.m. to 2:30 p.m.

Crop Hour
SDSU Extension Crop Hour webinars provide valuable information for South Dakota crop producers to help them improve their profitability and prepare for the upcoming season.

Smarter Farming Decisions Using ArcGIS and Satellite Imagery
How-to guide on using ArcGIS and satellite imagery to find value insights on crop performance.

Required Licensing For Applying Pesticide Using Spray Drones
Fact sheet for South Dakota stakeholders wanting to get certified to apply pesticides with a spray drone.

Integrating Precision Ag Tools for Smarter SCN Assessment and Management
Fact sheet on integrating Precision Ag tools for Soybean Cyst Nematode (SCN) assessment and management

Cybersecurity Planning: Securing the Future
With reliance on digital technologies, precision agriculture requires securing data and implementing key strategies to safeguard digital assets and maintain operational integrity and confidentiality.

Variations in a Field and Variable Rate Technology Adoption
Field variations, including soil properties, nutrient content, and moisture levels, can significantly impact crop yield and farm profits. By understanding the specific needs of different areas, farmers can apply fertilizers, seeds, and other inputs more effectively.
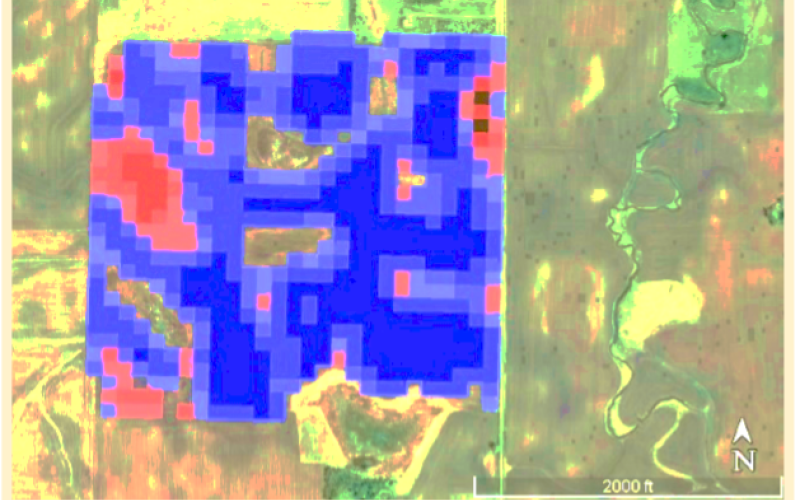
Satellite Farming: Download, Detect and Decide with Multispectral Imagery
Fact sheet about the benefits and accessibility of using multispectral imagery (MSI) from satellites and NDVI maps in modern farming.

Protecting Your Data: The Role of Authentication and Encryption in Agricultural Cybersecurity
Precision agriculture emphasizes using data to make smarter farming decisions. In the digital world, authentication and encryption are two prevalent ways to keep farm data secure, accurate, and trustworthy.

Digital Farming: Free Satellite Imagery & NDVI Maps
Fact sheet about the benefits and accessibility of using satellite imagery and NDVI maps in modern farming.