Cyber-attacks on agricultural systems have become an increasingly prevalent threat. These attacks can potentially cost farmers and agricultural companies millions of dollars and disrupt food supply chains. Though large corporations are often the primary targets of these attacks, anyone who is connected to the Internet is potentially vulnerable to hackers. Hackers employ a variety of tactics to gain access to electronic devices and steal user’s personal information.
One such type of attack is phishing attacks, where hackers attempt to trick individuals into revealing sensitive information such as passwords or credit card details by posing as a legitimate business or organization. To deploy phishing scams, hackers will send out hundreds to millions of fake emails that appear to be legitimate, hoping that some percentage of individuals will click on a link to a malicious website (the term "phishing" is derived from "fishing," illustrating the act of casting out bait and waiting for someone to bite). A popular form of phishing attack is referred to as ‘smishing,’ where hackers utilize text messages to get unsuspecting users to click on fraudulent links and give up personal or financial information. According to the Federal Trade Commission (FTC), bank impersonation is the most common text message scam, accounting for 10% of all smishing messages (SentinelOne 2024).
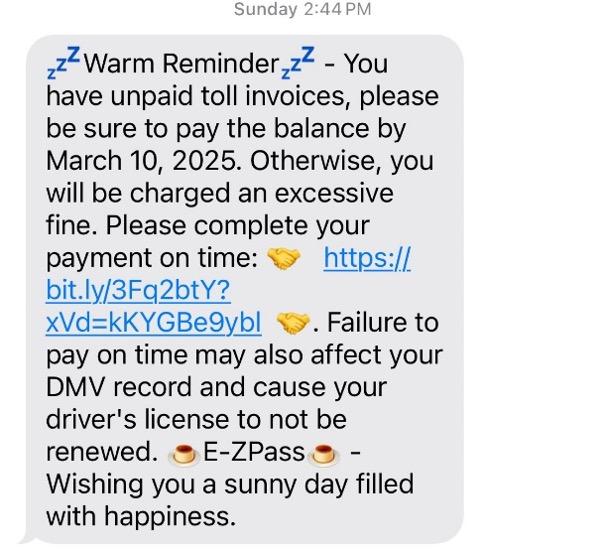
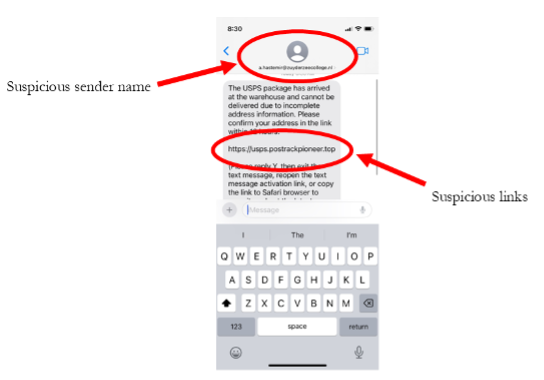
In smishing attacks, hackers send seemingly legitimate text messages, often impersonating a known entity like a business or government organization. These text messages often aim to create a sense of urgency and include links to fake websites that look real but are designed to steal login credentials or personal information. In the real example in Figure 1, a text message was sent pretending to originate from a ‘toll road company’ indicating unpaid invoices that must be settled within a few days to avoid or an excessive fine will be charged with possible consequences of losing one’s driver’s license. In another real example in Figure 2, a text message was received indicating a package couldn’t be delivered to your house with a link to confirm your address. In both of these instances, attackers are trying to create a sense of urgency so recipients will quickly click malicious links, allowing attackers to steal their personal information.
To protect yourself from these types of attacks:
Be suspicious of unsolicited text messages: Avoid clicking on links or providing personal information. Sometimes, links can also provide fake phone numbers to call where a real person will answer, these are also designed to steal your personal information.
Verify the source: If a message from a trusted source seems suspicious, contact the organization directly through their official website or phone number to verify the message.
Use Strong Passwords and two-factor authentication: This can help prevent hackers from gaining access if your information is compromised.
Report suspicious messages: Delete the suspicious text message and report it as spam to your service provider. You can also notify your local law enforcement, especially if you suspect fraud or identity theft.
