Written collaboratively by Xufei Yang, Ali Nafchi, Sushant Mehan, and Young Chang.
Precision agriculture (abbreviated as PA) is widely believed to fundamentally change how farming works in the future. Compared to traditional farming, PA emphasizes the importance of data and its efficient utilization, including data collection, analysis, interpretation, and delivery. Accordingly, PA highly relies on cyber-physical systems that bring together sensors, computers, the internet, and farm equipment. Despite the numerous benefits PA offers, it also brings some risks to farming practices. Like any complex machinery, the more complicated a system becomes, the higher the chances of encountering problems if not managed carefully. One prominent risk is cybersecurity, which involves malicious attacks on the cyber aspect of the PA systems. While other articles in this curriculum delve into specific cyber threats, this article aims to provide an overview of the basic structure of a PA system to enhance farmers’ understanding of potential cyber vulnerabilities.
Breakup of a Precision Agriculture System
Let’s demystify the workings of PA systems with fertilizer application as an example. In the traditional approach, you would start by taking soil samples from your crop field and sending them off to a lab for fertility analysis. Once the lab completes the analysis, they would either mail or email you the results. So far, you have handled data collection and delivery. Next, you would decide on the type and amount of fertilizers needed for your crops, relying on your expertise or seeking advice from SDSU Extension, NRCS, seed suppliers, and so on. This stage involves analyzing and interpreting the data to make decisions. Finally, you would load the selected fertilizers onto your applicator and adjust its settings to ensure that the right amount is applied to meet the crop’s nutrient needs in the field.
In the PA approach, this fertilizer application task becomes more informationized, automated, and computerized, yet the workflow remains similarly structured. We can break down any PA system, including fertilizer application, into four layers (Figure 1).
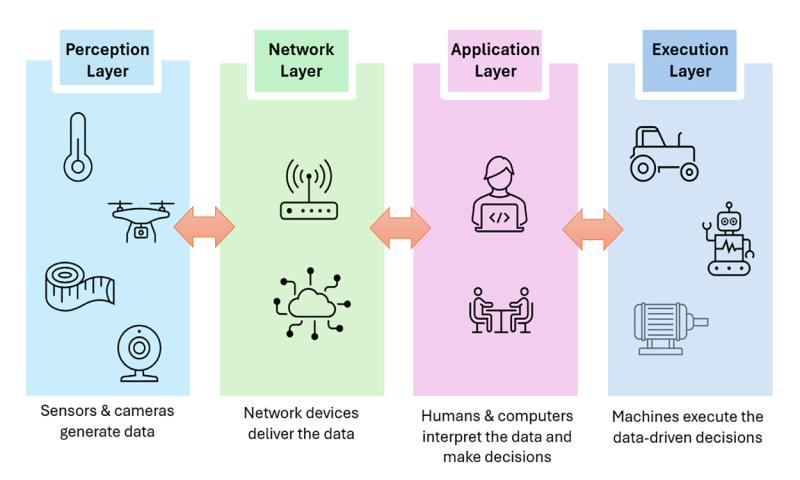
- Perception Layer: It involves data collection, but unlike the traditional approach, it emphasizes the utilization of sensors, unmanned aerial vehicles (abbreviated as UAV), satellite remote sensing, and more. In a PA system, soil fertility data may be obtained from soil sensors deployed across your crop field, or through UAV and satellite imageries.
- Network Layer: In a PA system, data is primarily delivered to its end users through wired or wireless communication networks. This not only improves the time efficiency of data delivery, but also enhances data integration and sharing among multiple users. For example, using field-deployed soil sensors, the fertility data can be transmitted to users via a local Long Range Wide Area Network (abbreviated as LoRaWAN) and then over the Internet.
- Application Layer: It involves human users and the computing devices (for example, computers and smartphones) they employ for data analysis and decision-making. Unlike the traditional approach, the decision-making process in a PA system relies on the support of these computing devices, which are typically connected to the network. For example, in fertilizer application, a producer can utilize a software program or web tool to determine the type and amount of fertilizers needed. In some cases (for example, ventilation of animal barns), management decisions can be solely made by computing devices.
- Execution Layer: This encompasses the utilization of machinery and actuators (for example, valves and relays) to implement the operational decisions formulated in the preceding stage. These machines or actuators may or may not be connected to the network. However, for those receiving commands and reporting their operating status through the network, they can be vulnerable to cyberattacks, despite offering significant savings on labor and time. In the example of the fertilizer application, the execution layer may involve a variable-rate applicator that is programmed using a computer.
Cyberattacks targeting any of these layers can compromise the integrity and functionality of a PA system, leading to serious consequences, such as partial or complete agricultural yield losses and the unauthorized disclosure of sensitive information. Meanwhile, given the variety of devices and equipment involved, PA encounters a wide array of cyber threats, as elaborated on by other articles within this curriculum. To enhance the reader’s understanding, these threats are categorized based on their target layers, as follows.
Perception Layer
As previously mentioned, this layer employs numerous measurement devices, including sensors and cameras, for data collection. Therefore, any disruption in device operation or any distortion of measurement outcomes, whether intentional or unintentional, could potentially result in misinformation guiding subsequent decision-making and execution processes. It is noteworthy that many measurement devices nowadays incorporate an embedded microcontroller or microcomputer for coordinating data acquisition, processing, and transmission, making them potentially more vulnerable to cyberattacks than traditional sensors.

Examples of cyber threats to the perception layer include, but are not limited to:
- Sensor malfunction: Apart from physical damage, sensor malfunction can result from inadequate installation, calibration, and maintenance. Particularly, for certain sensors, their calibration and troubleshooting are primarily conducted through the network. Accordingly, cyberattacks via a public network (like the Internet) could potentially compromise these sensors, resulting in data corruption, distortion, or losses.
- Sensor hijacking: Malware pre-installed on embedded devices or later infiltrated into them via the network can lead to the hijacking of sensors within a PA system. This could involve redirecting sensor readings to unauthorized users or denying authorized users access to the sensors. To mitigate this risk, farmers should acquire sensor and embedded device products from certified suppliers and avoid using third-party software programs.
- GPS jamming and spoofing: While both can jeopardize the functionality of GPS devices, GPS jamming disrupts GPS devices by flooding GPS satellite signals with artificial noise at the same radio frequency, whereas GPS spoofing involves the use of malicious GPS signal emitters that provide a GPS receiver with false location information.
- Sleep deprivation: Many sensors used in PA applications (for example, soil humidity sensors and GPS trackers) operate on battery power, consuming minimal energy during regular operation. To enable extended battery life, these sensors are typically programmed to enter a deep sleep mode when not in use. Sleep deprivation attacks disrupt this by keeping the sensors awake through repeated work requests, significantly reducing battery life.
Network Layer
A PA system may leverage multiple network technologies. Although the internet typically serves as the backbone of a network, other technologies, like 4G/5G cellular, Starlink, LoRaWAN, and/or Bluetooth might be integrated to extend network coverage. For instance, these technologies could connect sensors, cameras, machinery, and actuators in a crop field to the internet, broadening the system’s capabilities and reach. Depending on the network technologies, various cybersecurity challenges exist, alongside associated mitigation measures.

Typical cyber threats to the network layer include:
- DoS or DDoS attacks: A denial-of-service (abbreviated as DoS) attack intends to make a network resource inaccessible to its users, including farmers relying on a PA system, by disrupting the services of a host device, such as a computer or router, connected to the network. This is usually accomplished by maliciously overloading the device with excessive requests. A major distinction between DoS and Distributed Denial-of-Service (abbreviated as DDoS) attacks lies in the sources of these malicious requests: the former originates from a single source (or IP address), while the latter comes from multiple sources.
- Routing attacks: The primary function of network servers in a PA system is to oversee data flows and ensure they are routed to their intended destinations. A routing attack aims to disrupt routing paths, potentially blocking the forwarding of valuable data, either partially or entirely, or selectively directing certain data to their destinations while discarding others. Such attacks may lead to farmers receiving information incompletely, inaccurately, late, or not at all.
- Data transit attacks: These attacks aim to intercept and exploit data as they pass through the network. Two types of attacks may occur: packet sniffing and man-in-the-middle (abbreviated as MitM). Packet sniffing utilizes software programs or hardware to intercept data packets at specific nodes (for example, routers) on the network, while MitM attacks involve the insertion of malicious code between two parties on the network to monitor and manipulate their communications. Unencrypted data or networks are particularly vulnerable to these attacks.
Application Layer
The application layer is an essential component of a PA system, relying on the collaboration between humans and computers to handle data management, analysis, and interpretation. This layer usually involves demanding computational tasks, such as data fusion, statistical analysis, modeling/simulation, and artificial intelligence. It plays a pivotal role in making informed farming decisions that significantly impact agricultural productivity. However, given its reliance on human participation, it presents unique cybersecurity risks.

- Unauthorized access: Access control (abbreviated as AC) is essential to guarantee that only authorized users can access hardware (for example, farm computers) and software within the edge layer. A robust AC protocol should incorporate both physical security measures and user authentication. User authentication involves establishing and implementing strong password policies discussed in a separate article. Unauthorized access to critical software and hardware, whether intentional or unintentional, can severely disrupt farm operations.
- Signature wrapping: In this scenario, an attacker forges a digital signature to deceive the system. The signature appears valid during the authentication process but is accompanied by altered messages/commands. The alteration allows the attacker to potentially access sensitive data within a PA system. For instance, they could request that the data be redirected to a different recipient or processed differently from what is intended.
- Forged measure injection: This attack entails injecting fake, pre-created, or altered measurement data to misguide data analysis, interpretation, and subsequent decision-making processes. The injection can occur through various methods. For instance, it may involve inserting false data into a SQL database by modifying SQL queries, or sending a falsified data record that conforms to the required template or syntax to deceive a local server.
Additionally, since these computers are also integral parts of a network, they are vulnerable to DoS/DDoS attacks and MitM attacks, as introduced in the previous section.
Execution Layer
The execution layer, consisting of agricultural machinery and actuators, is the one most familiar to farmers. With technological advancements, a growing number of machines used for implementing PA management decisions may become network-connected. In practice, to facilitate network connectivity, many of these machines integrate microcontrollers or computers, making them potential targets for cyberattacks.

Cyber threats to this layer may include:
- Flash drive/SD card vulnerabilities: Although direct damage has not been widely reported, flash drives or SD cards used by many machines for data or code transfer can act as vectors for malware or spyware. A malicious file stored on the drive/card can potentially bypass even the most-secure networks, infecting crucial farm equipment. Moreover, these small memory devices are prone to being lost or stolen, resulting in the potential loss of sensitive information. This risk is significantly heightened when data on these devices remains unencrypted.
- Data cable vulnerabilities: Against common belief, cables used for charging and/or data transfer purposes can potentially be exploited by malicious hackers to attack machines. An example is the O.MG Elite cable, which resembles a regular-looking USB cable, but includes an embedded Wi-Fi module, allowing hackers to collect sensitive information from machines. Although no damage has been reported, this represents an emerging threat to agricultural machines or facilities where numerous cables are used on regular basis.
Apart from the above cyber threats, machinery and actuators in the execution layer may be additionally vulnerable to DoS/DDoS attacks, forged control injection (or insertion of malicious control commands), GPS spoofing, unauthorized access, and other risks, depending on the system architecture and configuration.
Summary
Given its heavy reliance on computers and computer networks (collectively known as cyberinfrastructure), PA presents various cybersecurity challenges to farmers. A typical PA system, which integrates physical and cyber components, consists of four layers: perception, network, application, and execution. Each layer is vulnerable to various cyber threats, as outlined in this article. Therefore, caution is needed when purchasing or deploying PA products or services on your farm. Beyond cost and performance considerations, the cybersecurity aspect of these products or services must be carefully assessed. As a farmer planning to adopt PA technologies, it is essential to define your expectations regarding data security, such as identifying sensitive information, before proceeding further. This article is not intended to discourage farmers from adopting PA technologies. Indeed, in many cases, the benefits of PA outweigh the challenges it presents. We recommend reading other articles in this curriculum to learn about specific cyber threat examples and their corresponding countermeasures.
References
- Alahe, M.A., Wei, L., Chang, Y., Gummi, S.R., Kemeshi, J., Yang, X., Won, K., Sher, M. Cyber security in smart agriculture: Threat Types, current Status, and future Trends. Under review.
- Bokka, R., & Sadasivam, T. (2024). Simulation-based Analysis of RPL Routing Attacks and Their Impact on IoT Network Performance. Journal of Electronic Testing, 1-15.
- de Araujo Zanella, A. R., da Silva, E., & Albini, L. C. P. (2020). Security challenges to smart agriculture: Current state, key issues, and future directions. Array, 8, 100048.
- Freyhof, M. (2022). Cybersecurity of Agricultural Machinery: Exploring Cybersecurity Risks and Solutions for Secure Agricultural Machines. MSc Thesis, University of Nebraska – Lincoln, Lincoln, NE.
- Tsiknas, K., Taketzis, D., Demertzis, K., & Skianis, C. (2021). Cyber threats to industrial IoT: a survey on attacks and countermeasures. IoT, 2(1), 163-186.

